Hikvision has recently been in the news thanks to revelations about its links to the Chinese government and the Communist Party of China. Naturally fears about whether they are compromised ‘by design’ have been raging on the Internet ever since. While there is no doubt that Hikvision is part-owned by the Chinese government, there has been no evidence yet of any backdoor or that Hikvision cameras are ‘dialing back home’ to their maker.
Okay but what could go wrong? Could a backdoor already exist in your Hikvision camera or NVR? Maybe. But so could your WiFi router or even your mobile phone. You are not about to stop using cell phones because the UK government (GHCQ) and the US government (NSA) are known to be able to hack into them, are you? So while its important to be aware that Hikvision is part-owned by the Chinese government, your best course of action is to take sensible precautions and not get too paranoid. Yep be reasonably paranoid but not tin foil hat paranoid!
So if you have Hikvision cameras, what should you do to protect them from hackers, spies or nosy governments? The following steps apply to any security camera, not just Hikvisions by the way:
A quick note: As an Amazon Associate I earn from qualifying purchases. This post contains affiliate link(s). An affiliate link means I may earn advertising or referral fees if you make a purchase through my link, at no extra cost to you.
Isolate all network cameras using Virtual LANs (VLANs)
The best way to achieve network security is by isolating your network cameras by creating Virtual LANs or VLANs.
A VLAN is a virtual group of network devices that physically may or may not be connected to a single network switch, but can be managed as if they are. Think of them as a way to segment your network into logical groups. The idea is to put your insecure network cameras in a virtual network which allows you to connect to the cameras but stops them from sending data out of that VLAN.
Your existing home router may already support VLAN creation. If not, the best way to implement VLANs is using a hardware device running a software firewall.
This could either be a DIY solution like a spare computer running pfSense, or a commercial ready-to-use product such as the Netgate SG-1100, or the versatile and powerful Ubiquiti Unifi Dream Machine Pro (UDM Pro).


Here’s my step by step guide for wired cameras and wireless cameras that shows how you can create VLANs with the Unifi gear.
Disable uPNP
uPNP or Universal Plug n Play was created to make life easier for us by letting various devices discover each other on a network and work with each other. Today as we edge into 2018, plug n’ play sounds like no big deal, hey when you plug in anything into a USB port, it just work right? Plug n’ Play. Simples.
Well there was a time, not so long ago, that 11 year old me tried to install a Plug n Play 56 kbps modem and trust me it was anything but Plug n’ Play. Things have come a long way since then and the stuff the uPNP can do is amazing, such as letting your computer automatically configure new printers. The same uPNP can also let security cameras auto-configure your WiFi router for remote access or cloud storage by setting up port forwarding without your help or even without your knowledge.
Hold on, so this very useful uPNP software can let my security cameras make outgoing connections without my explicit permission? uPNP was originally intended to let devices on a local network talk to each other, and that’s why the protocol doesn’t even have an authentication method by default. If all the devices involved were on your local network, this wouldn’t have been an issue. But as uPNP was extended to devices exposed to the Internet and used to automate port forwarding, various security implementations were created. Unfortunately many networking devices such as WiFi routers have flawed security implementations of uPNP and that’s why the US government recommends disabling uPNP altogether.
Here’s how you disable uPNP on Hikvision cameras and NVRs:
Log in to your Hikvision’s web admin page and navigate to Configuration > Network > Basic Settings > NAT. Make sure Enable uPnP is not ticked and click Save.
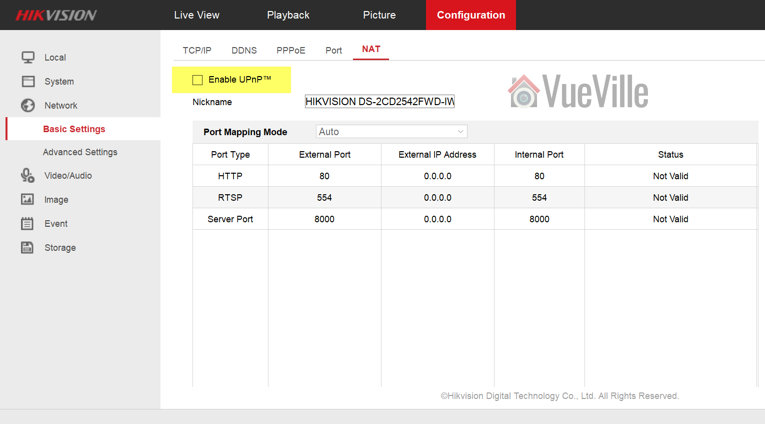
Disable P2P
The next one to disable is P2P. Hikvision calls it Platform Access. You will find this in Configuration > Network > Advanced Settings > Platform Access. Make sure the check box for Enable is not ticked and click Save.
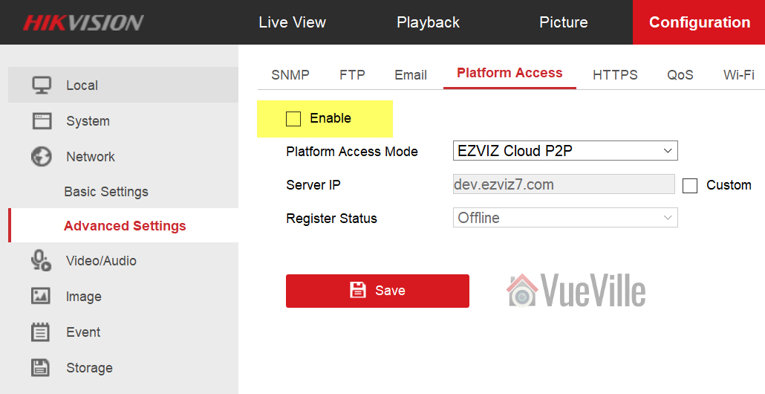
Also read:
Disable Anonymous Visit
You are going to find it under Configuration > System > Security > Anonymous Visit. Disable Anonymous Visit and click Save.
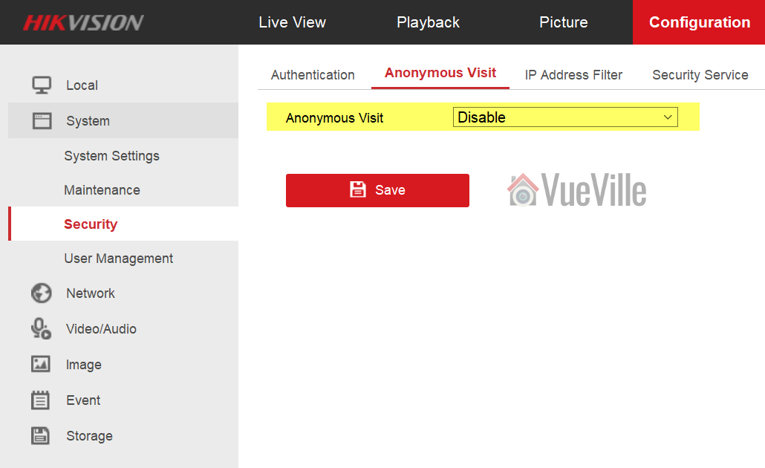
Disable SSH
You are going to find it under Configuration > System > Security > Security Service. Now uncheck “Enable SSH” and click Save.






I was testing the Hik this morning and it appears from my router logs that it’s connecting to Amazon’s servers when it sends a push notification.
Thanks for testing it, interesting find. That must be the Amazon AWS servers that a lot of companies use for their P2P and cloud services. I guess this sort of behaviour only emphasizes the point of my blog – these cameras really need to be locked down and isolated from the rest of your network if one values his/her privacy. I think I need to do the vLAN method sooner rather than later (and write a how-to).
Yeah, I double checked the Platform Access page under the “Network-Advanced Settings” menu, and the Enable button is not checked. On that page under “Platform Access Mode” the only option I have is “Hik-Connect.” But sure as anything, it’s still sending me those pushes. Just like Amcrest.
When I setup the Hik camera within their mobile iOS app, I used the home/local network ip address. I don’t have any DDNS enabled for the camera. And the only way when I’m in that app to connect to the live feed is to either to have my phone connected to my home network or to be connected to my router’s VPN when I’m out and about.
Very good to understand the underlying reasoning here. Incidentally, in the meantime I installed a Hikvision cam and downloaded their app iVMS-4500. It manages to do the same thing as Amcrest — it can get a push notification to my phone even when I’m not on my home network. I don’t have any of its ports forwarded either. And I think it’s locked down in a similar fashion to the way you described above, but it’s a slightly newer model and the menu options aren’t identical. I couldn’t find an option to enable/disable SSH and I couldn’t find anything about enabling or disabling anonymous user. But P2P and uPnP is disabled like above.
Sorry if I wasn’t clear earlier: P2P tech doesn’t need port forwarding at all and push technology uses P2P. P2P is the industry’s solution to avoid port forwarding, and to deal with the increasing possibility that port forwarding doesn’t work when more than one household shares the same external IPv4 IP address (because the Internet is running out of IPv4 addresses and ISPs assign the same IP addresses to more than one customer).
It is alarming to hear that the Hikvision (and Amcrest) are able to send you push notifications outside the home network even when P2P and uPnP are disabled. Make sure the ‘Platform’ option is also disabled, they keep renaming these things from firmware to firmware and I do not have a brand new Hikvision at hand to double-check. If it still manages to connect out (you can confirm using a wiretap software like WireShark), the only option left is to use a vLAN to restrict network access to LAN and not WAN/Internet.
My understanding of how push tech works is this: the main obstacle when your phone is outside the home network is that the Hikvision doesn’t know how to reach your phone. So the EZVIZ or HikConnect platform acts as an intermediary. The iVMS-4500 app on the phone connects out to the intermediary periodically and informs it how to reach your phone – this is an outgoing connection that your phone will see as ‘trustworthy’. Back home your camera will do the same – it will connect out to the intermediary whenever it wants to send a push notification. Since there are only outgoing connections at both camera and phone ends, port forwarding is avoided. I have omitted the steps above where the Hik mobile apps may use Apple’s or Google’s push service servers for getting as token to enable push on your mobile device in the first place.
This is a nice guide. I’m curious though — how do push notifications for motion events get through when your camera is locked down like this? I see on one screen you’re still forwarding certain ports. But for some reason I thought on another guide you wrote that you’re not forwarding any ports system wide anymore for security — rather just having everything behind the VPN. This is the thing I’m trying to figure out about your system.
Hi, this was a super helpful article, thank you! Any reason I wouldn’t see the Security tab at all on my admin page? I can’t find it or the sub categories anywhere. Also when I disable P2P it doesn’t allow me to see a live feed of my cameras in the app. Thoughts? Thanks in advance.
> Any reason I wouldn’t see the Security tab at all on my admin page? I can’t find it or the sub categories anywhere.
Are you sure you are logging in using an admin account and not a user/viewer account?
> Also when I disable P2P it doesn’t allow me to see a live feed of my cameras in the app. Thoughts?
You have probably set up the app with your camera using the P2P server option, rather than the local IP method. So if you disable the P2P service on your camera, the camera will stop reporting to the Hikvision P2P server and so your app stops working too.
So if you want to keep using live view but keep P2P disabled, you have only 1 option: Setup the app using the local IP of the camera and use a VPN to connect to your home network while out and about.
To learn more about P2P vs. VPN, read this article.
Hi Daniel,
Thanks for the extra info. I’m a bit concerned about the possibility that I’m not accessing the admin account if that’s correct. I trusted the installer get the software up and going for me and show me the ropes.
Do you know how I can verify if I’m using the admin account or how to fix that if not?
Thanks again for your help!
> Do you know how I can verify if I’m using the admin account or how to fix that if not?
In your camera settings (Configuration tab at the top of the camera’s web page), navigate to System > User Management. There you will see the ‘level’ of your user name – if its indeed an admin account you will see it here. This page also shows all other user accounts set up in the camera.
See screenshot here: https://www.vueville.com/wp-content/uploads/2022/11/Hikvision-Admin-Settings-Users-VueVille.jpg
If you are able to log into the camera’s web page but are not able to access any of the above settings, then you are logged in using an ‘Operator’ or ‘User’ account which are both beneath an admin account in privileges. You will need to contact your installer if this is the case.
Hi Brad, thanks for the comment! I minimise the number of holes I poke in my firewall for incoming connections. In fact there is just one – a custom OpenVPN port for the OpenVPN server. The reason I can lock down my cameras to the point that they cannot send anything out is because I do not make them send anything – they are not allowed to send email or push notifications.
So as you may have guessed I do not have push notifications enabled at all. I use my QNAP NAS Surveillance Station to send motion detection email alerts which are sufficient for my needs. I have not found a way to send push notifications without relying on an external cloud or P2P service, but then I have not researched this much as I don’t care for it.
I will be updating the security camera and home automation guides as I have now fully integrated these two sub-systems using what I call the pro-DIY approach to building a smart home.
Ah — for some reason I thought I read on here that you were NOT using QNAP to send notifications because it was unreliable, and instead were using Hikvision and its app to receive push notifications.
In the process of locking down an Amcrest PTZ POE camera (one you’ve mentioned) that I have, I have followed all of the above steps — whole network is behind router’s OpenVPN server in my case — and no ports are being forwarded. Yet — Amcrest’s app still manages in my case to break through to send push notifications for motion. Not sure how it’s managing that.
Just curious — you have a whole article about getting push notifications. Why have you now decided it’s not for you?
I haven’t tried QNAPs push service because it relies on their cloud platform.
While it is irritating that the Amcrest is still managing to connect out, this is less of a problem than Amcrest’s servers tunneling into your network using P2P which is what I would be worried about. By default, most routers allow all outgoing connections because the underlying assumption is that you trust all devices on your network. When this is not the case (as in my Hikvision cameras), I lock down their ability to make outgoing connections (dialing home to Hik servers). Most routers also block all incoming connections by default because this is where the bigger risk lies, hence the need to open ports using port forwarding.
The real solution to isolating a device on your network and cutting its internet access and allowing only LAN access is by using a firewall like pfSense to create vLANs (virtual LANs). This is one of my planned projects, I just need to make the time somehow!
I wrote about setting up push notifications because it was not easy to get them to work and I had readers asking me how to set it up. I never used them myself because email alerts are enough for me + I use just Imperihome for smart home control and quick camera viewing, and tinyCAM monitor Pro for more involved camera viewing. Lately I have become wary of letting any company’s P2P servers connect to my home network and this resulted in the post above.