One of the most common questions I have been getting about our DIY Home Security system is this: How to setup a VLAN and firewall rules to block IP cameras from accessing the Internet?
Wondering why you would want to do that? Here are a few good reasons:
- Most security cameras like to phone home to their manufacturer’s servers. There’s no need to, it’s not good for your privacy or your network’s security.
- Most security cameras have poor security and can be easily hacked, and none of us want someone spying on our indoor security cameras!
- Moreover, security cameras are at risk of being hacked to join botnets, which then attack other devices on your network or the Internet.
For the longest time, I was put off by my perception that firewalls and VLANs are too complex for me. Looking at most networking gear, I would be right.
The beauty of the Ubiquiti Unifi system I now use is that you don’t need to be a networking wizard to secure your security cameras and your home network. Using the excellent Unifi Controller GUI, I was able to block my security cameras from the Internet without getting a university degree in networking.
So in this tutorial, I am going to show you how to:
- Create a Virtual LAN (VLAN) for your wireless security cameras
- Create a dedicated Wi-Fi network for your wireless security cameras and assign this network to the VLAN
- Create 3 firewall rules to prevent the cameras accessing the Internet (but allow other devices on your network to access them locally or just for pulling the RTSP video streams)
NOTE 1: I use the example of wireless cameras in this how-to guide, see this guide for grouping wired cameras in a VLAN and blocking them from accessing the Internet.
NOTE 2: This tutorial is for those who only access their IP cameras via the local IP (such as 192.168.X.X). So for remote access, you would VPN into your home network and then access your cameras using their local IP address. If you require your cameras to be exposed to the Internet using P2P or DDNS, this tutorial is not for you! Most camera apps that have a plug ‘n play setup option use remote P2P servers! Blocking internet access to these cameras will cause them to fail.
Okay, so if you are accessing your IP cameras through the local IP address (from home or remotely via a VPN such as OpenVPN), let’s continue!
What you will need
You will need the Unifi UDM Pro which is a very versatile networking device along with at least one other Unifi Wi-Fi Access Point (WAP) such as the Unifi AP 6 Lite.
Preparation: Planning your home network
To make sense of this topic, we need a basic understanding of how network connections and firewalls work. I am assuming your security camera has an RTSP video stream and that’s what we are trying to view.
The relevant networking terminology is:
- WAN (Wide Area Network) refers to the Internet.
- LAN is your local home network.
For simplicity, let’s assume your mobile phone is connected to your general Unifi Wi-Fi network. In the Unifi world, your phone is therefore in the LAN group. By default, devices in the LAN group can access any part of the local network and the Internet.
When you use your mobile phone IP camera app (like tinyCAM Monitor Pro) to view the stream of your wireless IP camera, the phone sends an RTSP connection request to your IP camera. The camera accepts it and sends the stream back out to your phone.
Now, the idea here is to segment your home network into different groups, based on what type of access control you want to impose on those devices. In networking parlance, you would create a Virtual LAN or VLAN to group these devices together.
When you create a VLAN in the Unifi Controller software and assign a device to it, the router will tag each data packet of that device with a VLAN ID.
How do VLANs work in practice? How do I assign a device to a VLAN?
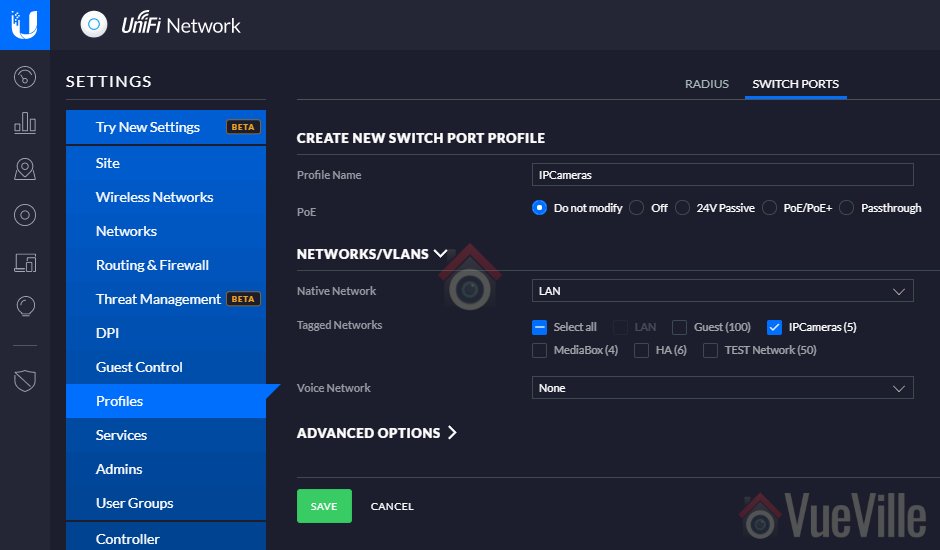
For wired devices, you can assign each port of a managed switch to a specific VLAN. Then all devices connected to that network will be in the same VLAN. That’s what happens with a Unifi Switch. So if you connect your wired PoE IP cameras to a port that’s assigned to VLAN 25, all those IP cameras are now in VLAN 25.
For wireless devices, you create separate Wi-Fi networks for different groups of devices and then assign a VLAN ID to each Wi-Fi SSID you create. So you would create a Wi-Fi network called ‘IP Cameras’, assign that Wi-FI SSID to VLAN 35, and connect all your wireless cameras to that network. All those wireless cameras are now in VLAN 35.
Then you can create firewall rules for each VLAN to control data flow in very granular detail (if you choose to!).
In summary, segmenting your home network into different VLANs allows you to precisely control how and where data is allowed to go.
Further reading: Unifi Guide to VLANs
What are some good ways to group devices?
For example, you may want your media boxes to reach the Internet to access Netflix, Amazon Prime, Hulu etc. But you may not want them to access the rest of your network. Why? Because your cable provider’s cheap no-name box probably has weak security and may be the easiest way for hackers to get inside your home network. So that’s one VLAN for your media boxes.
If you are using wired PoE cameras outside your home, anybody can access your entire home network through that network cable! So you should put wired cameras also into their own VLAN and isolate it from the rest of your network.
Its also a very good idea to make all your security cameras fully local by blocking them from the Internet. Many of them phone home regularly and are also easy targets for botnets and the like.
I have created separate VLANs for my PoE cameras and Wi-Fi cameras. I also have separate VLANs for my home automation system and the default VLAN Unifi created for the guest Wi-Fi network. Please note that I have an older Unifi setup that involves a USG and switch combo, which you can simply replace with a single Unifi UDM Pro device!
What’s in scope of this tutorial
To keep this tutorial easy to follow and understand, I am not going to show how to replicate my entire network setup. That would be a 10,000 word post at least and this tutorial is already long enough as it is!
You will learn the core ideas here and then you can create more VLANs and more firewall rules to suit your specific needs. Just ask me in the comments section if you have any questions.
If you want your camera to send ONVIF motion detection notifications to your NVR, you need to create additional firewall rules to allow outgoing connections from the camera’s ONVIF port (usually port 80, some Reolink cameras use port 8000). Consult your IP camera manual to see which ports are used for these features.
Step 1. Create a VLAN for your security cameras
For simplicity, I will take the example of creating a VLAN and Wi-Fi SSID for wireless cameras.
In the Unifi world, a VLAN is the same as a ‘network’. So you have to create a ‘network’ with a VLAN ID of your choice.
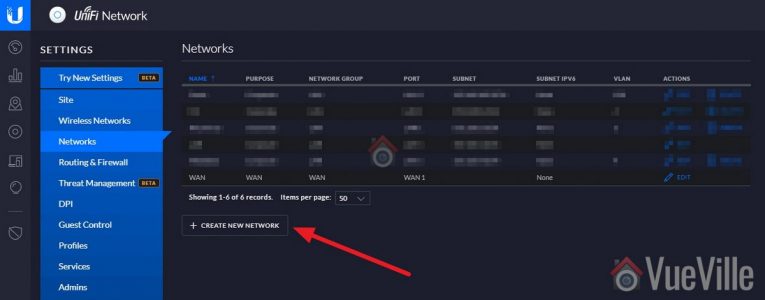
- Log into your Unifi controller and navigate to Settings > Networks. I am using the classic settings view.
- Click on ‘ + Create New Network’

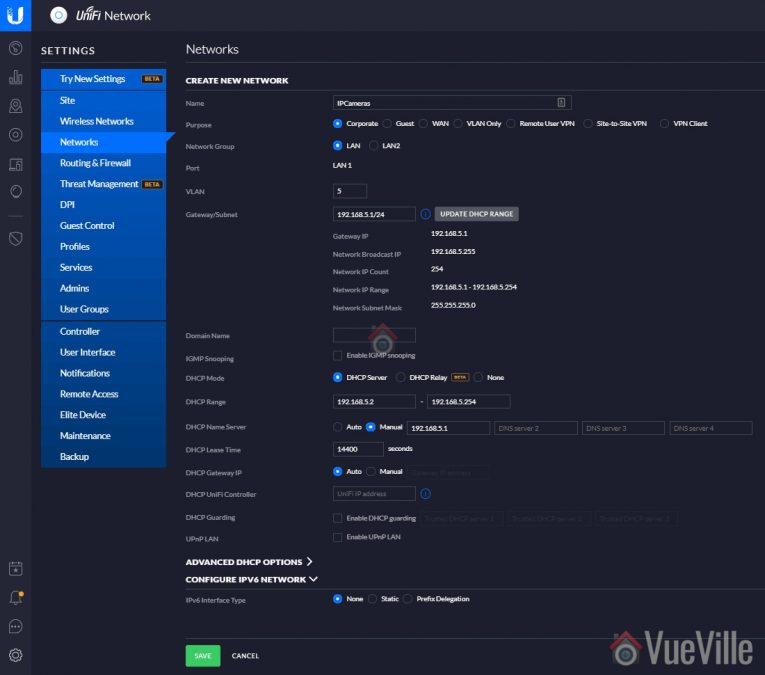
- Enter a name, I chose ‘IPCameras’

- Leave all the settings at defaults except the following
- VLAN: Select a number, I used 5 as per my home network plan. For convenience, it’s a good idea to keep the VLAN ID same as the subnet you choose in the next step.
- Gateway/Subnet: My main network is 192.168.1.X, so I chose a subnet of 192.168.5.X for this VLAN. So enter your desired subnet followed by ‘/24’. So I entered: 192.168.5.1/24
- DHCP Range: 192.168.5.2 – 192.168.5.254 (replace 5 with your selected subnet number)
- DHCP Name Server: Choose manual and enter 192.168.5.1 (replace 5 with your selected subnet number)
- DHCP lease time: 14400 sec
- Hit Save
Step 2. Create a dedicated Wi-Fi network for your security cameras
Next let’s create a Wi-Fi SSID for your wireless cameras to connect to, and assign this SSID to the ‘network’ created earlier.
- Navigate to Settings > Wireless Networks. I am using the classic settings view.
- Click ‘+ Create New Wireless Network’

- Under the ‘Create New Wireless Network’ section
- Expand the ‘Advanced Options’ section to reveal it
- Select VLAN and enter the VLAN ID you have chosen. I entered 5.
- Hide SSID – select this for better privacy
- If you have created a user group, you can assign one here. Useful for bandwidth rate limiting etc but not relevant in our case.
- Combine Name/SSID: Select this. If your camera supports the 5 GHz band, it will be used instead of the slower 2GHz band. Most security cameras do not.
- Leave all other settings at default

- Hit Save
Wait a few minutes for the Unifi controller to provision the new wireless network.
Note: If you are looking to use only wired cameras, the concept remains the same but in this step 2 you will tag specific Unifi switch ports with the VLAN ID from step 1. Here’s a tutorial on grouping wired PoE cameras into a VLAN.
Step 3: Create 3 Firewall rules to block camera access to the Internet
We will create 3 firewall rules for our security camera VLAN and those rules will apply to all the cameras in this VLAN.
The logic behind our firewall rules
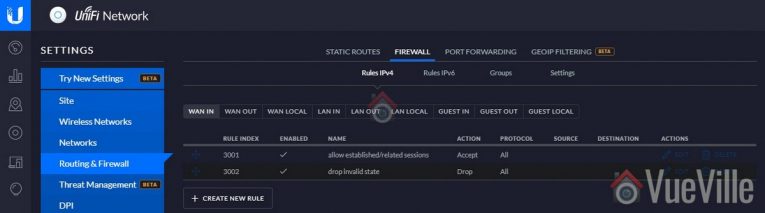
We will be editing the WAN OUT (connections going out to the Internet), and LAN OUT (connections going from inside a VLAN to the rest of your local network or Internet). We will use the default rules for LAN IN (connections coming into a VLAN from the rest of your local network or the Internet):
- We do not want our cameras to accept connections from the Internet. We want to allow only connections from the local network. You can achieve both of this through a single firewall rule, but we don’t need to create it manually. The Unifi USG firewall by default ‘drops’ or ignores all unsolicited incoming connections from the Internet. Any good firewall will do this by default. You can find this default rule under then WAN IN section of the firewall rules.
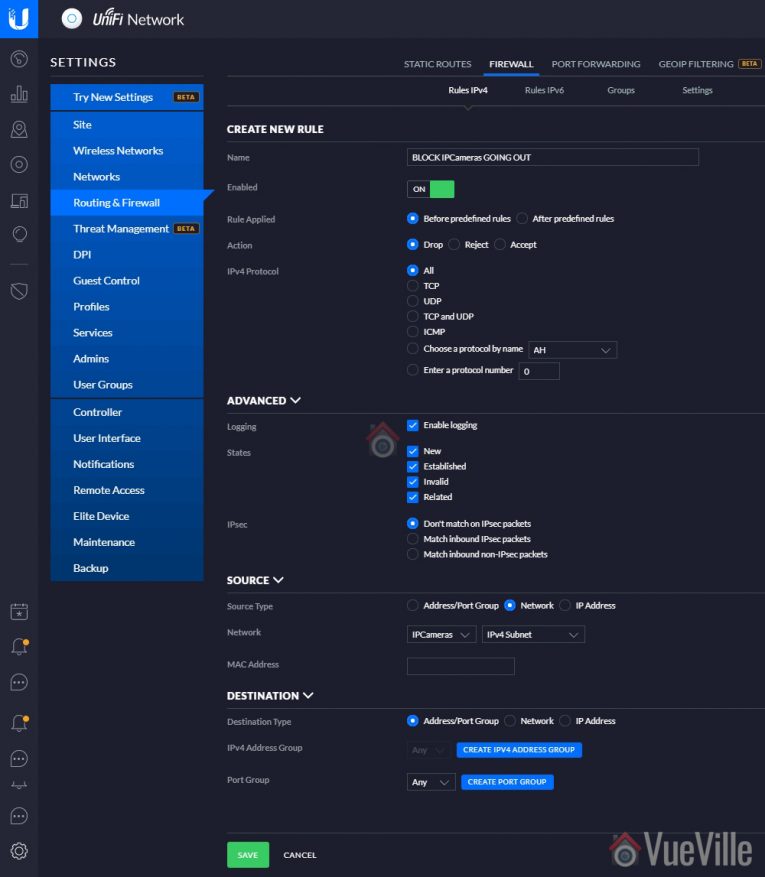
- We also do not want the cameras to initiate connections to the Internet (WAN). In other words, we do not want them to ‘phone home’ to the manufacturer’s servers. So we will define a WAN OUT rule blocking all outgoing connections initiated by this VLAN. That’s Rule 1.
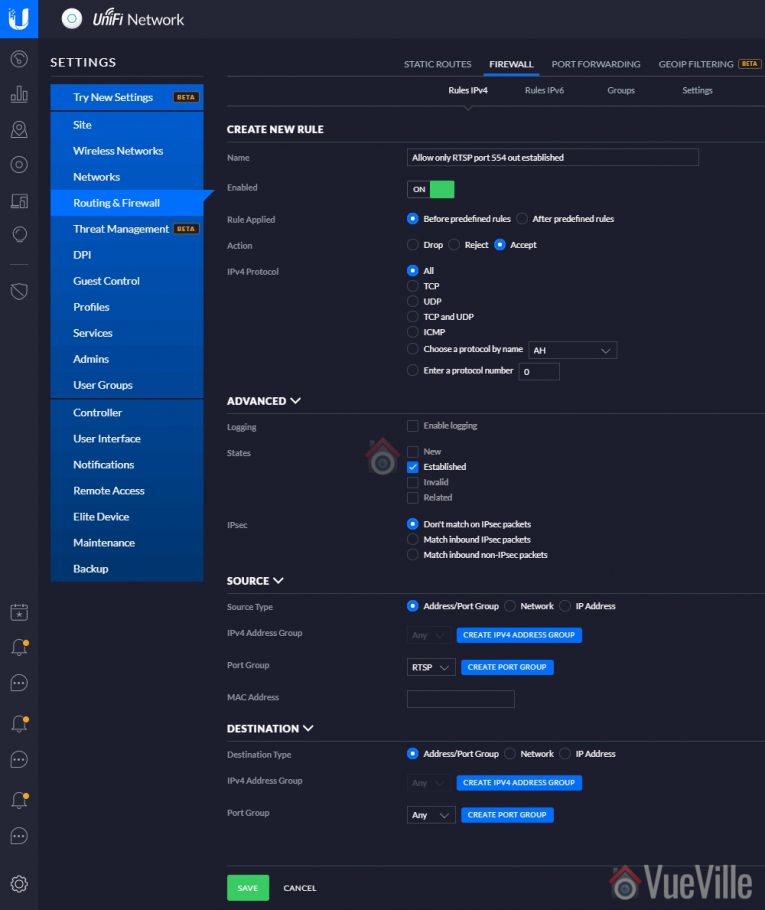
- To further tighten up things, even when a connection request is received by this VLAN from anywhere else in the local network, I want the firewall to allow the cameras only outgoing RTSP connections. That’s another LAN OUT rule and rule no.2 for today.
- We also don’t want the cameras to initiate any other connection to the rest of the local network (LAN). So we will define a LAN OUT rule blocking all outgoing connections initiated by this VLAN. That’s Rule 3.
Whom this tutorial/approach is not for
Do you want to use your camera manufacturer’s P2P-based mobile app (Dahua P2P, Reolink P2P etc.)? Then this tutorial will not help you – blocking Internet access for the cameras will kill the P2P feature also.
This tutorial is only for those who only want to use the RTSP video stream of their cameras (use all 3 rules below) OR want to use a mobile app set up using a local IP address (use only rule 1 below).
Creating the rules
Right, let’s do it.
- Navigate to Settings > Routing & Firewall. I am using the classic settings view.
- Select the Firewall tab and then Rules IPv4

- Rule 1 – Block access to the Internet (WAN)
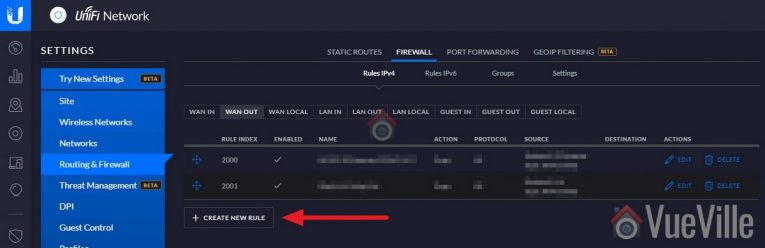
- Select the WAN OUT tab, and click ‘+ Create New Rule’

- Name this rule ‘Block IPCameras going out’

- Under Advanced, enable logging and select all the states
- Under Source, select Network and pick the VLAN network you created earlier (IPCameras in the step 1 above). Ensure IPv4 subnet is selected in the dropdown next to it.
- Leave everything else at defaults
- Hit Save
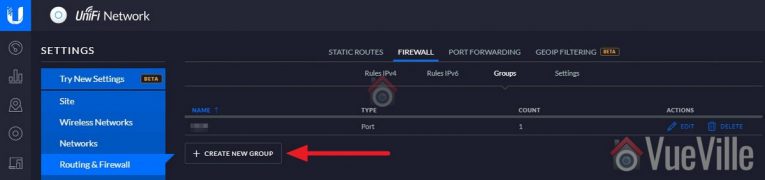
- Select the WAN OUT tab, and click ‘+ Create New Rule’
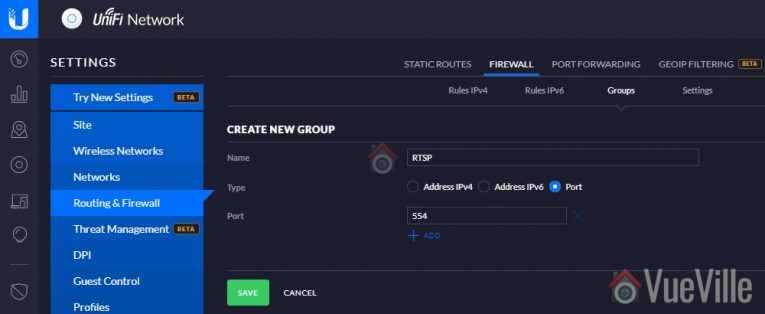
- Create a port group for rule 2
- Rule 2 – Allow only RTSP outgoing connections in response to incoming requests from the LAN
- Rule 3 – Block access to the rest of your home network (LAN)
- Select the LAN OUT tab, and click ‘+ Create New Rule’
- Name this rule ‘Drop all outgoing’

- Under Advanced, select all the states
- Under Source, select Network and pick the VLAN network you created earlier (IPCameras in the step 1 above). Ensure IPv4 subnet is selected in the dropdown next to it.
- Leave everything else at defaults
- Hit Save
The order of these rules is very important – after creating the rules above, make sure that under the ‘LAN OUT’ section rule 2 is on the top of the list and rule 3 should be after it. Because that’s the order in which the firewall will process the rules.
Now let’s test the rules to see whether they are working as intended. Temporarily connect a laptop or mobile phone to the Wi-Fi SSID you created. You should not be able to reach the Internet or access any other local network resource such as the Unifi controller dashboard. If all is well, disconnect from the Wi-Fi network.
Now simply connect your wireless cameras to the Wi-Fi SSID. Re-connect your mobile phone or laptop to your regular Wi-Fi network. Now try to access the RTSP stream of your cameras – you should get a video stream.
Congratulations! You have now secured your security cameras and your network is a whole lot safer.











Thanks so much for creating this tutorial with detailed explanations and instructions. I’m using multiple wired and wireless cameras which are sharing RTSP streams and event notifications to a QNAP NAS QVR Pro application. Using your approach, the cameras are on a separate VLAN and isolated from the WAN.
Following your instructions, the QNAP QVR Pro application can view streams but no longer captures them using event settings. I created a rule to allow LAN out Port 80 traffic and expected this would solve the problem. But it didn’t.
All my cameras are Amcrest. AFAIK they all use port 554 for RTSP (which is working via your instructions) and (I think?!) port 80 for event reporting. They are setup in QVR Pro by their camera names — not as generic ONVIF.
Hi Greg, you are on the right track. You need to log in to your Amcrest camera’s web admin and check what ports it is set up to use. This is explained in this Amcrest video at the 1 min mark: https://www.youtube.com/watch?v=qbXHQqGgZKs
You can see the camera example in the video uses ports 37777, 37778, and 37779 for http instead of port 80. Try opening all of the ports listed on your camera admin page.
If none of this helps, try allowing port 8080 – this is used by some cameras for ONVIF event reporting instead of 80.
Woot! Yup, that did it. My cameras showed port 80 for http but 37777 and 37778 for TCP and UDP respectively. Opening 80, 37777, and 37778 for LAN OUT re-enabled event reporting from the Cameras to the NAS.
Excellent! Glad that worked, I will add your scenario to the article for others who may face the same issue.
Hi Daniel,
So how does this work for sending push notifications and emails with screenshots and the like when motion detection is triggered? If the cameras can’t access the internet, how does this work?
Hi my cameras do not send any alerts at all – my QNAP NAS running QVR Pro software is doing all of that.
Hi Daniel,
Thank you for the guide. I’ve got several Hikvision cameras set up, but there seems to be one hitch: whenever a device first tries to connect to the cameras, RTSP isn’t enough. I don’t know what protocol it uses, but whenever I power on or connect a new device to the network, the “Drop all outgoing” rule prevents it from connecting to the cameras. If I temporarily disable the rule, connect, then re-enable it, then it works like a charm. Still, it’s annoying if there’s an extended power outage, or if I need to check the cameras from a different laptop or whatever. Any idea what protocol it specifically needs to connect, so that I can keep the firewall rule while still allowing unimpeded connections?
Interesting, I haven’t had this issue with my cameras. But then I set them up from a VLAN which had the rule active right from the start. Are you setting up your cameras via the P2P option as opposed to a fully local setup?
Nope, it’s fully local. I’ve got the cameras on a VLAN while the NAS and other devices are on the default network.
Great guide. Thank you.
I found a problem though: since I needed to use the camera app on my mobile device to configure the camera (to choose the new VLANed SSID), but the new VLAN only allows RTSP traffic, the app is stuck and can’t choose the new SSID… I think I’d need to do all setup steps (to create the VLAN/SSID), connect the camera to the new VLAN (with the new IP address), and THEN lock it down with the rules. Will try that soon.
Yes you should configure the camera before activating the firewall rules – but do note that you can turn each rule ON or OFF at any time in the Unifi firewall setup page. So just switch off the rules if you have already created them and turn them back on after you are happy with the camera setup.